Step 1 – Configure Server Profile used to send SYSLOG messages to a destination
Note: The Palo Alto Administrators guide states that by default all log data is forwarded over the MGT interface. In addition, we will have to create a Server Profile for external services the firewall will interact with.
From your web based management console navigate to Device -> Server Profiles -> Syslog. You’ll configure the name, ip address or fqdn of the syslog server, port, and format. Typically syslog messages are sent over UDP to port 514 in a BSD format. IETF format is normally used over TCP/SSL.
Step 2 – Enable Log Forwarding
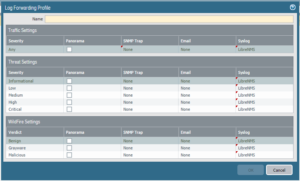
Navigate to Objects -> Log Forwarding.
We create a Log Forwarding Profile that specify ServerProfiles that we will be sending event logs to in the form of SYSLOG and SNMP messages. You can control a severity threshold to define when messages are forwarded out of the palo alto to your log collector.
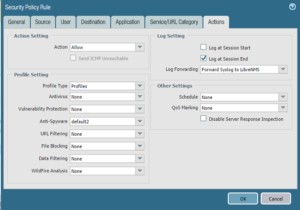
Step 3 – Add Log Forwarding Profile to a Security Rule
In this example I have created a security rule that governs DNS traffic that is generated in our LAN and is destined for the Internet. My thought is I would like to receive notice when any user on my network tries to resolve a URL while avoiding our internal DNS servers. I edit this “Deny DNS Out” rule, navigating to the Actions Tab where we specify a Log Forwarding Profile created in step 2.