I recently had need to reconfigure LDAP settings on a Palo Alto firewall. I had retired two production domain controllers and stood up two new boxes in their place. Remote access VPN users are authenticated by the firewall via LDAP on port 389, or LDAP over SSL (LDAPS) on port 636.
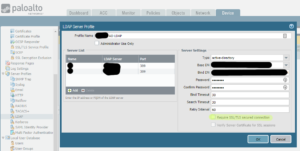
The quickest solution was to provide the firewall with the FQDN, IP Address, and port numbers needed to communicate with the new domain controllers using the LDAP protocol. Ensure ‘Require SSL/TLS secured connection’ is not selected
I make this note as I had assumed the new domain controllers were talking LDAPS by default but I was wrong. A quick look over the authentication log, authd.log, using the command > tail follow yes mp-log authd.log, revealed this:
2018-07-11 09:05:04.826 -0500 Error: pan_authd_ldap_bind(pan_authd_shared_ldap.c:615): Failed to bind ldap (Can't contact LDAP server) 2018-07-11 09:05:04.826 -0500 Error: pan_auth_create_a_ldap_session(pan_auth_svr_cctxt.c:1971): Failed to bind, get out 2018-07-11 09:05:04.827 -0500 debug: pan_auth_response_process(pan_auth_state_engine.c:4073): auth status: auth server not available
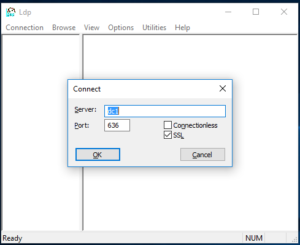
A more secure implementation would take advantage of LDAPS. In a nutshell, you will need to generate your own self-signed certificate, or better, install a certificate provided to you by a CA. Also, LDP.exe is a helpful utility that can verify a successful connection or binding to your directory. It can be obtained by downloading the Microsoft Remote Server Administration Tools (RSAT)
In this post I’ll review configuring my new domain controllers with self-signed certificates in lieu of obtaining signed certificates from a CA. To start, open Server Manager on a new domain controller and install the Active Directory Certificate Services role. As you proceed through the wizard, be sure to configure AD-CS as an Enterprise, Root CA.
Open the Certificate Templates Console: Launch mmc.exe and add the Certificate Templates snap in and click OK. In the left pane of the snap in right click the domain controller and click View Object Identifiers. In the dialog window, scroll down to the Server Authentication Policy and ensure the Object Identifier is displayed as 1.3.6.1.5.5.7.3.1.
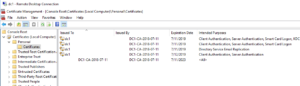
Add the Certificates snap in to MMC and instruct the Certificates snap in to manage certificates for the Computer account. Expand the Personal folder in Certificates snap in and right click on the Certificates sub folder, select All Tasks -> Request New Certificate. Select Active Directory Enrollment Policy and click Next. Select Domain Controller and click Enroll. Once finished you’ll see a certificate issued to each domain controller in the domain. You can view these new certificates now in the Local Computer Certificate Store, specifically within the Personal->Certificates sub-node.
At this point, your domain controller should be configured to respond to connection attempts using LDAPS. You can verify this using the LDP.exe utility from Microsoft.
Resources:
How to Troubleshoot LDAP Authentication
Configuring Secure LDAP Connection on Server 2016